Osmedeus allow you automated run the collection of awesome tools to reconnaissance and vulnerability scanning against the target.
Tuesday, April 2, 2019
Monday, April 1, 2019
Commando VM - The First of Its Kind Windows Offensive Distribution

Welcome to CommandoVM - a fully customized, Windows-based security distribution for penetration testing and red teaming.
Using HTTP Pipelining to hide requests
In this post I'm going to discuss using HTTP pipelining to hide malicious HTTP requests. This is not domain fronting but uses similar techniques to get the same result, an observer who is not able to perform TLS interception is only able to see the "good" request which conceals the "bad" request.
Sunday, March 31, 2019
How To Increase Jio 4G Net Speed Upto 80 Mbps, 7 Awesome Tricks

How To Increase Jio 4G Net Speed Up to 80 Mbps, 7 Awesome Tricks: So you got Jio 4G sim card and are you looking to increase the internet speed of your jio sim. Then you came to right place.
OWASP A10-Unvalidated Redirects and Forwards

Web applications often redirect and forward users to other pages and websites, and use untrusted data to determine the destination pages.
Flightsim - A Utility To Generate Malicious Network Traffic And Evaluate Controls

flightsim is a lightweight utility used to generate malicious network traffic and help security teams to evaluate security controls and network visibility. The tool performs tests to simulate DNS tunneling, DGA traffic, requests to known active C2 destinations, and other suspicious traffic patterns.
Thursday, March 28, 2019
Wednesday, March 27, 2019
How to Perform Manual SQL Injection While Pentesting With Single quote Error Based Parenthesis Method
If you are trying to hack the databases with methods like single quotes error based injection, Integer based injection or double quotes method but the databases are not vulnerable to those methods injection will fail and you cannot connect with database.In short, the error based Manual SQL injection will use single quote to break the query and join the query, Integer based injection will be joining the query without the single quote and double quotes will be joining the query with double quotes.
What is XSS (Cross Site Scripting) ? – A Detailed Understanding the Type of XSS
XSS is a very commonly exploited vulnerability type which is very widely spreadand easily detectable and also it is one of the important vulnerability in OWASP TOP 10.
Mobile Device Security Checklist
We often get asked for things we can do to help users keep their mobile devices secure. Here's a quick list of some simple things you can do to ensure that your mobile devices are running with at least some security. All of these steps are free and raise the bar on both unauthorized use of your device and the integrity of the applications you're running on them. Our goal here is not to make your device impenetrable to attack, but instead to raise the bar.
So You Wanna Be a Pen Tester? 3 Paths To Consider (Updated)

It's an exciting time to be a professional penetration tester. As malicious computer attackers amp up the number and magnitude of their breaches, the information security industry needs an enormous amount of help in proactively finding and resolving vulnerabilities. Penetration testers who are able to identify flaws, understand them, and demonstrate their business impact through careful exploitation are an important piece of the defensive puzzle.
How to Use Nmap with Meterpreter
You’ve sent your phishing ruse, the target has run the Meterpreter payload, and you have shell on their system. Now what? If you follow our blogs, you probably have quite a few ideas! One thing that I don’t typically do is port scan other systems on the network. There are a few reasons for this. Port scanning is quite noisy, many IDS packages are set to quickly alert on these activities, and most of the time it isn’t needed to achieve my goals. Regardless, let’s say that you do find yourself in a situation where you do need to find services on other systems. Maybe you’re on a segmented network, you’ve gained shell on a jump host, and now you want to explore the new world that has just opened up to you. There are a few options out there that you can utilize.
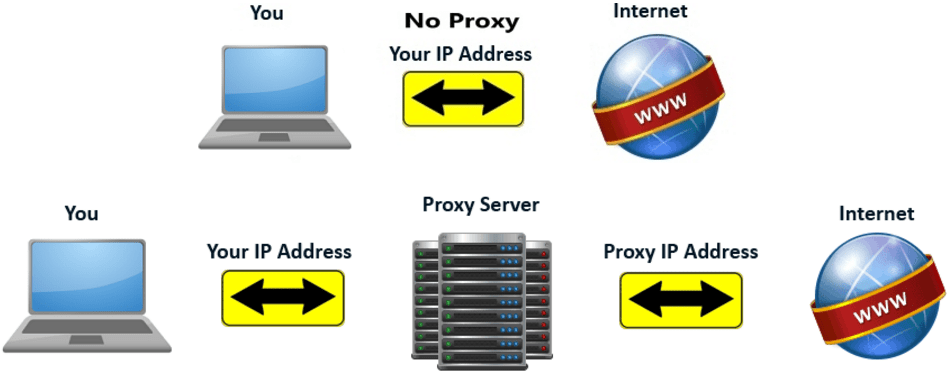
How to rotate your source IP address
I was on an engagement recently that was blocking my password sprays based on my IP address. If I made 3 incorrect requests from my IP I was blocked out from making any other requests for 30 minutes. How annoying is that? It is a great form of security and it might stop attackers looking for a quick way in. But, this form of security shouldn’t be viewed as a way to stop all password spraying. It won’t stop a dedicated hacker, one really trying to get access to your environment.
Subscribe to:
Comments (Atom)
Osmedeus - Fully Automated Offensive Security Tool For Reconnaissance And Vulnerability Scanning
Osmedeus allow you automated run the collection of awesome tools to reconnaissance and vulnerability scanning against the target. ...

-
flightsim is a lightweight utility used to generate malicious network traffic and help security teams to evaluate security controls an...
-
You’ve sent your phishing ruse, the target has run the Meterpreter payload, and you have shell on their system. Now what? If you follow...
-
Now if another day new entry, in the blog this time with a collection of Pentesting Bookmarks that I found in code.google which has ...